
Secure Your Digital Footprint: How to Safeguard Against Data Leaks in Mobile Applications

Secure Your Digital Footprint: How to Safeguard Against Data Leaks in Mobile Applications
Quick Links
- Keep Tabs on Your Phone’s Permissions
- Check the Privacy Dashboard
- Stop Google Collecting App Data
- Revoke Permissions for Unused Apps
- Uninstall Unused Apps
- Check an App on Exodus Privacy Before Installing
- Only Install Apps From Verified Sources
- Review an App’s Permissions Before Installing
- Read App Privacy Policies
Key Takeaways
- Check app permissions regularly to control access to the camera, microphone, and files.
- Use Android’s Privacy Dashboard to monitor app permissions and restrict abusive access.
- Remove unused apps and only install them from certified sources to safeguard your data.
These days, smartphones can do it all. Unfortunately, they can also track it all. Smartphones have become a data mining gold mine, but you’re not powerless—there are things you can do to make yours less accessible and valuable to those who seek profit from your activity.
The steps and screenshots shown below are from a Google Pixel phone. The exact location of these settings may be different on your device, but you can also search the settings app to find things more easily .
Keep Tabs on Your Phone’s Permissions
There are certain parts of your phone that apps have to request permission to access. An app cannot open the camera unless you first give it permission. It cannot access the microphone. It cannot search through your files.
Some of the apps that your phone came with may have permissions that you wish to revoke, or you may have granted undesirable permissions to apps you installed without paying much attention. You can change this by opening Settings > Security & Privacy > Privacy > Permission Manager.
Close
Check the Privacy Dashboard
Since Android 12, phones come with a feature known as the Privacy Dashboard . The Privacy Dashboard shows not only which apps have what permissions but also how often and how recently they’ve accessed them. You can click on an app that seems to be abusing its privileges and prevent it from having access in the future.
Go to Settings > Security & Privacy > Privacy > Privacy Dashboard. Here is how to access the privacy dashboard on a Samsung device .
Close
## Stop Google Collecting App DataWhen you first set up an Android device, if you say yes to every question Google asks during setup, you will supply the search giant with a lot of information about you. Fortunately, you can tell Google not to collect this information. In some cases, such as your web browsing and YouTube viewing history or your location data, you can even tell Google to delete it. You can also set up an auto-delete schedule so that Google can only save recently generated data.
You can audit these options by going to Settings > Security & Privacy > Privacy > Activity Controls.
Close
Revoke Permissions for Unused Apps
While it’s helpful to check permissions every few months periodically, that’s often not something we’re going to remember to do. Thankfully, Android can automatically revoke permissions for apps that haven’t been used in a while.
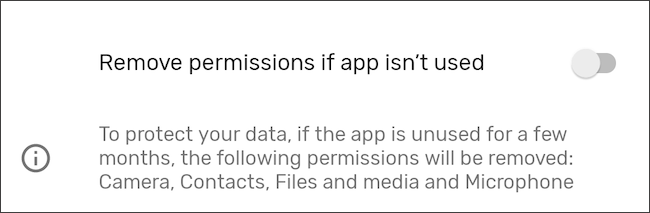
On newer phones, this feature may already be enabled. To be sure, go to Settings > Apps and select an app. Scroll down to “Pause App Activity if Unused” and activate the toggle. In addition to revoking permissions, this will also delete temporary files and stop notifications from said app.
On a Samsung device, the steps are the same, but the wording has been changed to “Remove Permissions if App is Unused.”
 ZoneAlarm Pro Antivirus + Firewall NextGen
ZoneAlarm Pro Antivirus + Firewall NextGen
Uninstall Unused Apps
Many apps that we want or need tend to collect a lot of data in the background. Some social networking, video streaming, shopping, image editing, and other such apps can track what we do with our phones even when not in use. We may accept this quietly when an app provides functionality that we are using often, but if we are no longer using an app, there’s no reason to let it continue quietly sucking up this data .
Scroll through your app drawer and take note of which apps you no longer use—then remove them . You can do this by holding down an app icon and selecting “App Info.” Then, hit the uninstall button. On some phones, you can just press down on an icon and select “Uninstall.”
Check an App on Exodus Privacy Before Installing
Permissions tell you a lot, but they don’t tell you the whole story. They tell you mechanisms that an app can use for tracking, but they don’t tell you whether an app actually is. That’s where Exodus comes in. This is an Android app auditing service that comes from a nonprofit based in Europe.
You can check whether an app contains known trackers by heading to the Exodus search tool and entering the app’s name. Exodus also provides a free and open source app that can automatically scan the apps already on your device. The Exodus app is available in the Play Store and on F-Droid .
Only Install Apps From Verified Sources
Out of the box, you can only install apps from pre-certified app stores like the Play Store and the Galaxy Store. If you try to install an Android APK file directly from your web browser or from a third-party source like TapTap , your phone will try to block this install. That’s because many malicious apps are distributed as APKs that would not be safely allowed in the certified app stores.
For most people, sticking to the default stores is a pretty good rule of thumb. Yet this is not to say that people, especially more technical users, should never install apps from alternative places (some third-party sources like the free and open-source F-Droid repositories are arguably safer sources of software than the Play Store). Rather, do your due diligence, and be sure to only install software from places you can trust.
Review an App’s Permissions Before Installing
You can actually view which permissions an app will require directly inside the Play Store before you even install it. This way, a greedy program never even sets foot on your device.
Scroll down to “About This App” on the Play Store listing, then scroll again to “App Permissions” and tap “See More.” Here, you can view the permissions that the app will request access to after installation.
Close
Read App Privacy Policies
Many apps come with a privacy policy, especially if the app is an anchor to an online service. While it is tempting to check the necessary boxes during the initial launch and move on with your life, at least give the privacy policy a quick skim. You will sometimes see something that you really aren’t comfortable with.
A smart home app, for example, might show that it not only collects your IP address and your physical location but that it may share this information with third parties for advertising purposes. That means you aren’t just giving that information over to one company but sales companies, data brokers, or tech giants like Google and Facebook, who are known to buy up data from other sources. A privacy policy won’t come right out and say that its service is shady, but it sure might imply it.
Performing all of these steps won’t guarantee your privacy, but it will help. To take things further, you can use a VPN to mask your IP address . You can also use email aliases when signing up for new apps. And if you really want to be certain nothing is going on in the background, you can install a firewall like NetGuard.
Also read:
- [New] Add Transitions in Kinemaster
- [New] How to Connect Instagram to Facebook for 2024
- [Updated] A Deep Dive Into Panasonic's HX-A1 Camera Features for 2024
- [Updated] Screen Savants A Comprehensive Guide to HD Recorders
- 2024 Approved Auditory Artifacts Essential Ringtone Archives Online
- 2024 Approved Thorough Examination Capturing Life in Full with Gear 360
- 3 Ways of How to Get Someones Apple ID Off iPhone 12 mini without Password
- A Comprehensive Walkthrough of the Arlo Defense System
- Achieve Full Control with Admin CMD Role
- AMD Quality Computer System Builders Race Event, Q4 2015 - Competitive Price at Just $912
- Apex Spectrum by Maingear: Combining Customizable RGB Lighting with Advanced Liquid Cooling Features
- Decrypting Diablo 2'S Hiccups: Effective Ways to Stop Your Game From Crashing
- Discover the New Dawn of Computing with Intel's Bean Canyon NUCs - Superior Speed & Throttled TDP
- Ease Your Build Process with the Innovative Features of Asus TUF Gaming Desktops
- Enhance Academic Performance with These 6 Essential PC Improvements for Students
- Enhanced Power and Efficiency: Intel Unveils High-Performance Bean Canyon NUCs
- Exclusive 'Tom's Hardware' AMA Event Featuring AMD Insights – Join Us This April 6Th!
- Exploring Computer Components with Tom’s Hardware Experts
- Exploring Digital Innovations with Tom's Hardware Review Guide
- Exploring Technology with Tom's Hardware Insights and Analysis
- Exploring Technology with Tom's Resource: Hardware Breakdown and Reviews
- Exploring Tom's Tech Insights: A Guide to the Latest in Computer Hardware
- Hands-On with Technology: Tom's Detailed Insights on Electronics
- How to Fix Zoom Error Code 1132 in Windows 10 & 11
- How to Navigate Apple's Podcast Acceptance Policy
- How Will US Import Duties Impact the Cost of Electronic Components & Personal Computers? Unraveling the Complexity
- In 2024, 2 Ways to Transfer Text Messages from Honor Magic 6 to iPhone 15/14/13/12/11/X/8/ | Dr.fone
- In 2024, How to Remove Apple iPhone 11 Activation Lock
- In 2024, Portable Battery Packs to Keep Recording Longer
- In 2024, Top 12 Prominent Honor Play 8T Fingerprint Not Working Solutions
- Introducing MSI's Innovative '#YesWeBuild' Campaign - A Fresh Take on PC Creation
- Introducing the Qualcomm Snapdragon Development Board: Bridging Microsoft Windows and ARM Technology
- Launching MSI's Unique 'YesWeBuild' Movement: Embracing the Future of Computer Building
- Mastering Custom Interactions with GPT-3: Top 5 Techniques Revealed
- Mastering Hardware with Tom's Expertise - The Definitive Tech Resource
- Microsoft Unveils Windows Support for Qualcomm's New ARM-Based Snapdragon Developer Platform
- Navigating Computer Hardware with Tom: Your Ultimate Guide
- Navigating Gadget Innovation with Tom: Expert Analysis & Comparisons for Smart Shoppers
- Quiet Powerhouse Creation: The Journey to an RGB-Less, Whisper-Quiet Computer - Insights From Tom's Hardware
- Refine iPhone Image Capture Specialized Filming Tools
- Seamless Switches Expert Advice on Changing Your Wallpapers in Win11 for 2024
- Skylake System Construction Showdown: Announcing the Champions of Tom’s Hardware Competition
- Skylake System Construction Showdown: Announcing the Champions of Tom’s Hardware Competition!
- The Best iSpoofer Alternative to Try On Tecno Camon 20 Pro 5G | Dr.fone
- The Ultimate DIY: Constructing an Ice-Chilled Living Room Computer Tower - Expert Tips From Tom's Hardware
- Tom's Computer Review: The Ultimate Guide to Tech Innovations
- Tom's Gadget Analysis: In-Depth Evaluation of Latest Electronics and Specs
- Tom's Tech Hub: Expert Insights and Comprehensive Reviews
- Tom's Tech Hub: Expert Insights Into Computer Components and Systems
- Tom's Tech Insights: Expert Reviews and Guides
- Tom's Tech Insights: In-Depth Hardware Reviews & News
- Tom's Tech Insights: The Ultimate Guide to Computer Components
- Tom's Tech Review: In-Depth Analysis and Insights
- Tom's Tech Reviews: In-Depth Guides & Insights on Computer Hardware
- Top Redux Masterpieces of 2016 - We're Accepting Entries Now!
- Two Ways to Sync Contacts from Tecno Camon 20 Premier 5G to Gmail | Dr.fone
- Unveiling the Best in Gadgets and PC Hardware with Tom's Guide
- Upgrade Your Workstation: Essential Z790 Motherboards and Liquid CPU Coolers Reviewed
- Which Pokémon can Evolve with a Moon Stone For Lava Agni 2 5G? | Dr.fone
- Win a Top-Ranked PC Building Contest: Tom's Hardware Exclusive
- Winner Highlights From the 2015 Fourth Quarter at Tom's Hardware: System Builder Showdown Results
- Title: Secure Your Digital Footprint: How to Safeguard Against Data Leaks in Mobile Applications
- Author: Kevin
- Created at : 2024-08-28 04:23:15
- Updated at : 2024-08-29 04:23:15
- Link: https://hardware-reviews.techidaily.com/secure-your-digital-footprint-how-to-safeguard-against-data-leaks-in-mobile-applications/
- License: This work is licensed under CC BY-NC-SA 4.0.


.png) Kanto Player Professional
Kanto Player Professional DLNow Video Downloader
DLNow Video Downloader